一、背景介绍:
当前腾讯云私有域VPCDNS暂时还不支持背景下,租户业务上自建DNS解析服务就成了硬需求。本文介绍在腾讯云CVM环境下搭建内网解析。
实现功能:
1. 支持腾讯云云环境保留域名解析 如: mirrors.tencentyun.com ;
2.支持用户自有业务域名内网解析 如: you.aaa.com ;
3.支持访问外网域名解析 如:www.qq.com ;
4. 支持分域名转发到不同的DNS-server;
基础环境:
CVM: 标准型SA2 (请根据自身业务情况,选择机型)
OS: CentOS Linux release 7.6.1810 (Core)
BIND: bind-9.11.4-16.P2.el7_8.6.x86_64
二、安装配置:
1. #yum install -y bind bind-chroot bind-utils
2. 主配置文件 /etc/named.conf
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.html
options {
listen-on port 53 { 127.0.0.1;172.16.3.82; }; #82为CVM内网IP
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
recursing-file "/var/named/data/named.recursing";
secroots-file "/var/named/data/named.secroots";
allow-query { any; }; #开放查询
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes; #允许递归
dnssec-enable no;
dnssec-validation no; #这个配置非常重要,关闭dnssec检测
forward only;
forwarders{
183.60.83.19; #腾讯云VPC环境下默认DNS地址(直接cat /etc/resolv.conf 获取)
183.60.82.98; #腾讯云VPC环境下默认DNS地址
};
/* Path to ISC DLV key */
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
#测试域名(用户业务内网解析域名)
zone "aaa.com" IN {
type master;
file "aaa.com.zone";
};
#增加依据不同的域名转发到不同的后端DNS-Server
zone "qq.com" IN {
type forward;
forward first;
forwarders {8.8.8.8;};
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
[root@DNS1]#
3.编写zone文件:
# cat /var/named/aaa.com.zone
$TTL 1D
@ IN SOA @ root.aaa.com. (
0
1D
1H
1W
3H )
@ IN NS dns
dns IN A 127.0.0.1
www IN A 1.2.3.4
you IN A 1.71.3.4
4. 测试检查配置文件
# named-checkconf -z /etc/named.conf
# named-checkzone aaa.com.zone /var/named/aaa.com.zone
5. 启动服务
# systemctl start named
三、测试验证:
模仿业务机测试
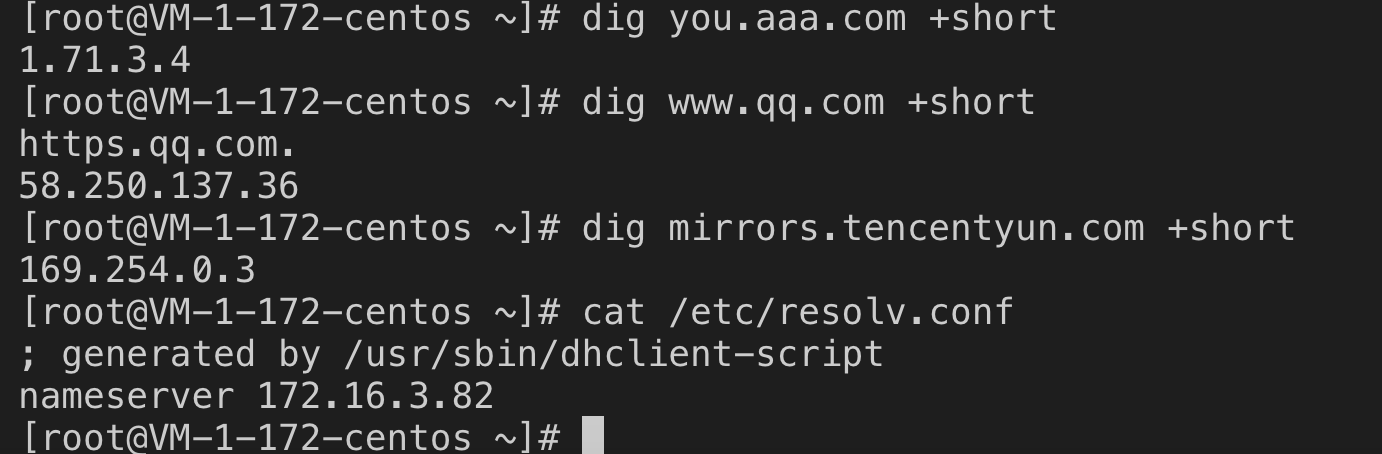
测试符合预期
备注:
1. 如发现异常请优先检查CVM云主机安全组配置。 2.该方案仅用于自建内网DNS解析做参考。如希望提供公网递归解析服务需符合相关政策法规,可参阅:https://cloud.tencent.com/document/product/213/35533