什么是Ingress
当你在Kubernetes集群中运行多个应用程序时,每个应用程序都有自己的服务。为了让外部用户访问这些应用程序,就好像他们访问网站一样,我们需要一种方法来管理流量的分配和路由。这就是Ingress的作用。
想象一下,您的Kubernetes集群就像一个大型的公寓楼,每个公寓是一个应用程序。而Ingress就是大楼的大门,允许外部人员进入。大门上有一个保安,他会检查来访者的目的地,并根据他们的要求告诉他们去哪里。
Ingress就是这个保安,他知道应该将来自某个网址的请求引导到特定的应用程序。这可以通过不同的规则来实现,就像保安知道哪个公寓对应哪个房间号一样。这样,当人们访问不同的网址时,保安就会将他们引导到正确的应用程序。
要使保安工作,您需要在大门口放置一个标志,告诉保安如何引导来访者。在Kubernetes中,这个标志就是Ingress对象。而控制这个保安的是Ingress Controller,它就像是保安的老板,负责确保保安按照标志上的规则来引导人们。
总而言之,Ingress就是一种管理外部流量的方式,它允许您告诉集群如何将请求引导到正确的应用程序,就像大门保安将人们引导到正确的公寓一样。这使得外部用户能够方便地访问您在Kubernetes中运行的不同应用程序。
高可靠Ingress架构
高可靠架构首先解决的就是单点故障,通常在Kubernetes中采用多副本部署方式,同时由于Ingress作为集群流量接入口,建议采用一个Ingress服务独占一个Ingress节点的方式,以避免业务应用与Ingress服务发生资源抢占。架构图如下:
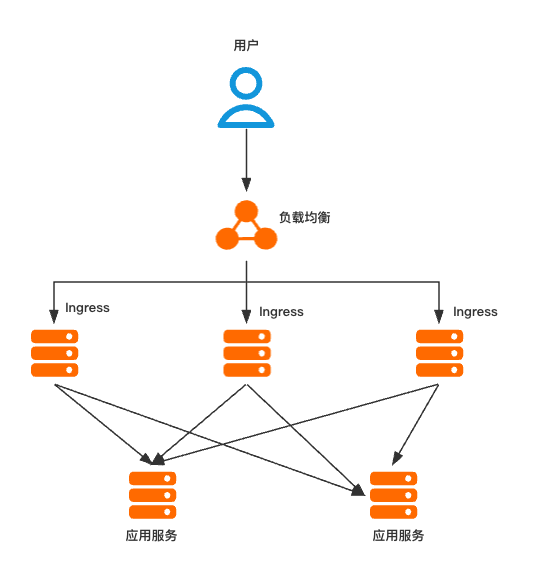
部署高可靠Ingress
环境介绍
$ kubectl get nodes
NAME STATUS ROLES AGE VERSION
cluster-control-plane Ready control-plane 4m5s v1.27.3
cluster-control-plane2 Ready control-plane 3m47s v1.27.3
cluster-control-plane3 Ready control-plane 2m59s v1.27.3
cluster-worker Ready <none> 2m50s v1.27.3
cluster-worker2 Ready <none> 2m52s v1.27.3
cluster-worker3 Ready <none> 2m54s v1.27.3
cluster-worker4 Ready <none> 2m52s v1.27.3
cluster-worker5 Ready <none> 2m54s v1.27.3注:当前环境为kubernetes v1.27.3
版本选择
选择Ingress-nginx最新版本1.8.1,支持的kubernetes 1.27,1.26, 1.25, 1.24版本
Ingress-NGINX version | k8s supported version | Alpine Version | Nginx Version | Helm Chart Version | |
|---|---|---|---|---|---|
🔄 | v1.8.1 | 1.27,1.26, 1.25, 1.24 | 3.18.2 | 1.21.6 | 4.7.* |
🔄 | v1.8.0 | 1.27,1.26, 1.25, 1.24 | 3.18.0 | 1.21.6 | 4.7.* |
🔄 | v1.7.1 | 1.27,1.26, 1.25, 1.24 | 3.17.2 | 1.21.6 | 4.6.* |
🔄 | v1.7.0 | 1.26, 1.25, 1.24 | 3.17.2 | 1.21.6 | 4.6.* |
🔄 | v1.6.4 | 1.26, 1.25, 1.24, 1.23 | 3.17.0 | 1.21.6 | 4.5.* |
v1.5.1 | 1.25, 1.24, 1.23 | 3.16.2 | 1.21.6 | 4.4.* | |
v1.4.0 | 1.25, 1.24, 1.23, 1.22 | 3.16.2 | 1.19.10† | 4.3.0 | |
v1.3.1 | 1.24, 1.23, 1.22, 1.21, 1.20 | 3.16.2 | 1.19.10† | 4.2.5 | |
v1.3.0 | 1.24, 1.23, 1.22, 1.21, 1.20 | 3.16.0 | 1.19.10† | 4.2.3 | |
v1.2.1 | 1.23, 1.22, 1.21, 1.20, 1.19 | 3.14.6 | 1.19.10† | 4.1.4 | |
v1.1.3 | 1.23, 1.22, 1.21, 1.20, 1.19 | 3.14.4 | 1.19.10† | 4.0.19 | |
v1.1.2 | 1.23, 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.18 | |
v1.1.1 | 1.23, 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.17 | |
v1.1.0 | 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.13 | |
v1.0.5 | 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.9 | |
v1.0.4 | 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.6 | |
v1.0.3 | 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.5 | |
v1.0.2 | 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.3 | |
v1.0.1 | 1.22, 1.21, 1.20, 1.19 | 3.14.2 | 1.19.9† | 4.0.2 | |
v1.0.0 | 1.22, 1.21, 1.20, 1.19 | 3.13.5 | 1.20.1 | 4.0.1 |
安装 Ingress
# 安装ingress $ kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.8.1/deploy/static/provider/cloud/deploy.yaml namespace/ingress-nginx created serviceaccount/ingress-nginx created serviceaccount/ingress-nginx-admission created role.rbac.authorization.k8s.io/ingress-nginx created role.rbac.authorization.k8s.io/ingress-nginx-admission created clusterrole.rbac.authorization.k8s.io/ingress-nginx created clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission created rolebinding.rbac.authorization.k8s.io/ingress-nginx created rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx created clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created configmap/ingress-nginx-controller created service/ingress-nginx-controller created service/ingress-nginx-controller-admission created deployment.apps/ingress-nginx-controller created job.batch/ingress-nginx-admission-create created job.batch/ingress-nginx-admission-patch created ingressclass.networking.k8s.io/nginx created validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission created查看安装状态
$ kubectl get deploy,pod -n ingress-nginx
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/ingress-nginx-controller 1/1 1 1 75sNAME READY STATUS RESTARTS AGE
pod/ingress-nginx-admission-create-qf7ln 0/1 Completed 0 74s
pod/ingress-nginx-admission-patch-7nxmr 0/1 Completed 0 74s
pod/ingress-nginx-controller-79d66f886c-v5d9f 1/1 Running 0 74s
如上状态,说明安装成功
到此为止,Ingress安装成功了!
Ingress HPA
一般情况下,Ingress已经有足够能力应对业务的突发情况,为了避免高负载情况下仍然不满足需求,我们可以通过HPA进行对Ingress进行水平扩容,接下来我们来配置一下,
# 安装metrics-server$ kubectl apply -f https://github.com/kubernetes-sigs/metrics-server/releases/latest/download/high-availability-1.21+.yaml
serviceaccount/metrics-server created
clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created
clusterrole.rbac.authorization.k8s.io/system:metrics-server created
rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created
clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created
clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server created
service/metrics-server created
deployment.apps/metrics-server created
poddisruptionbudget.policy/metrics-server created
apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created创建HPA
$ cat hpa.yml
apiVersion: autoscaling/v2
kind: HorizontalPodAutoscaler
metadata:
name: ingress-nginx-controller-hpa
namespace: ingress-nginx
spec:
scaleTargetRef:
apiVersion: apps/v1
kind: Deployment
name: ingress-nginx-controller # Deployment Name
minReplicas: 3 # 最小副本数
maxReplicas: 6 # 最大副本数
metrics:
- resource:
name: cpu
target:
averageUtilization: 80 # 阈值
type: Utilization
type: Resource
$ kubectl apply -f hpa.yml -n ingress-nginx
horizontalpodautoscaler.autoscaling/ingress-nginx-controller-hpa created
最佳实践
接下来,咱们通过最佳实践,验证一下ngress的功能是否正常!
# 部署应用
$ cat deployment.yml
apiVersion: apps/v1
kind: Deployment
metadata:
name: demo
labels:
app: demo
spec:
replicas: 1
selector:
matchLabels:
app: demo
template:
metadata:
labels:
app: demo
spec:
containers:
- name: demo
imagePullPolicy: Always
image: registry.cn-shanghai.aliyuncs.com/kubesre01/demo:v1
ports:
- containerPort: 8080
apiVersion: v1
kind: Service
metadata:
name: demo-svc
spec:
type: ClusterIP
selector:
app: demo
ports:
- port: 8080
targetPort: 8080
$ kubectl apply -f deployment.yml
deployment.apps/demo created
service/demo-svc created
创建ingress对象
$ cat ingress.yml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: demo
spec:
rules:
host: demo.kubesre.com # 访问域名
http:
paths:path: /info # uri
pathType: Prefix # 匹配方式
backend:
service:
name: demo-svc # Service Name
port:
number: 8080 # Service访问端口
ingressClassName: nginx
$ kubectl apply -f ingress.yml
ingress.networking.k8s.io/demo created
pathType:参数说明:
- ImplementationSpecific:对于这种路径类型,匹配方法取决于 IngressClass。 具体实现可以将其作为单独的 pathType 处理或者与 Prefix 或 Exact 类型作相同处理。
- Exact:精确匹配 URL 路径,且区分大小写。
- Prefix:基于以 / 分隔的 URL 路径前缀匹配。匹配区分大小写,并且对路径中的元素逐个完成。 路径元素指的是由 / 分隔符分隔的路径中的标签列表。 如果每个 p 都是请求路径 p 的元素前缀,则请求与路径 p 匹配。
访问:
# 出现如下信息,说明访问成功了
$ curl demo.kubesre.com/info
{"message":"云原生运维圈!"}总结
本文介绍了什么是Ingress,以及高可用部署解决了哪些问题并通过实战进行讲解,接下来文章内容中会分享更多企业级实战案例,请敬请期待!