用户名:admin
旧密码:Admin@123
新密码:Huawei@123
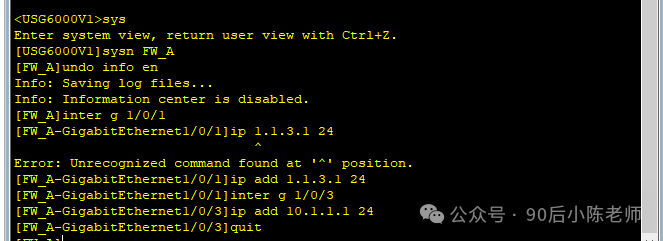
步骤1:防火墙A的网络基本参数
(1)接口IP地址
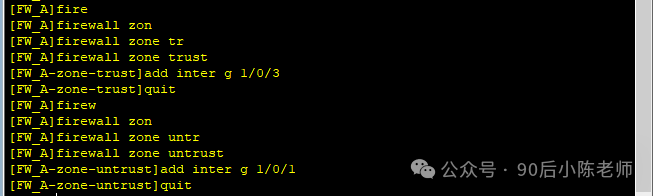
(2)接口加入安全区域
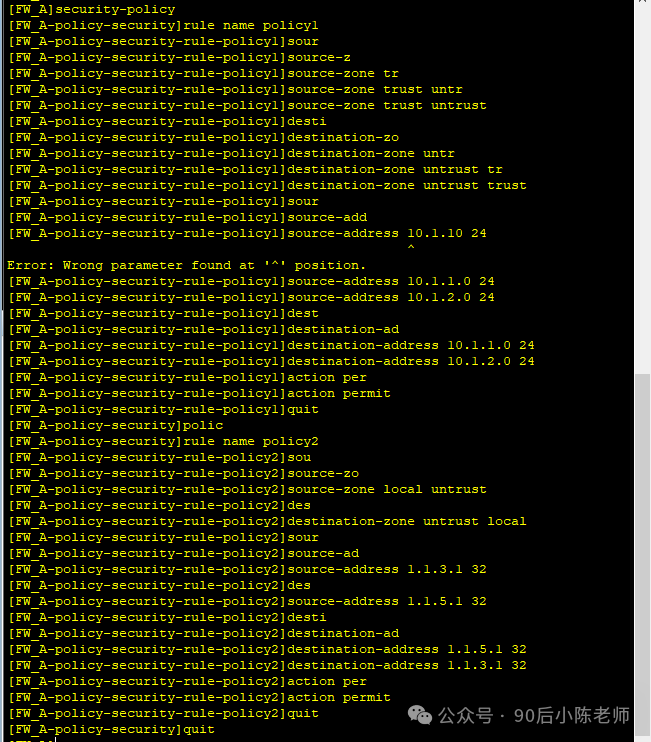
(3)安全策略
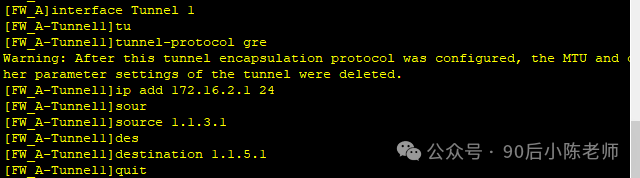
步骤2:防火墙A配置GRE
(1)Tunnel接口的相关参数
(2)接口加入安全区域
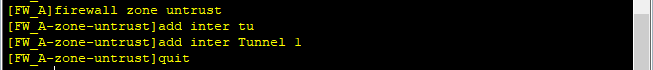
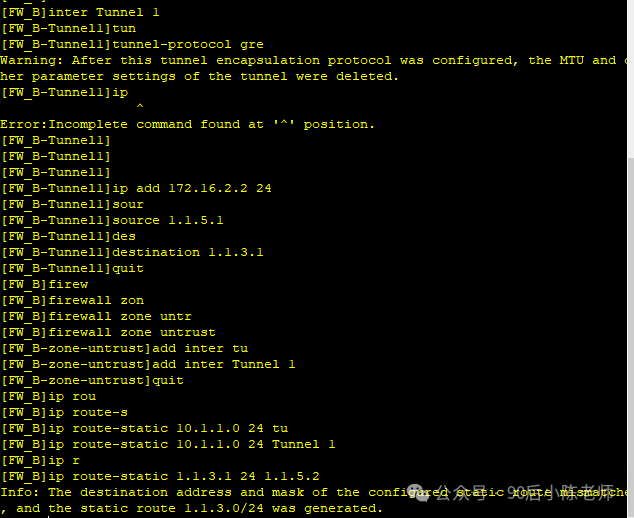
步骤3:防火墙A配置路由

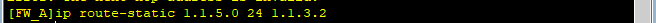
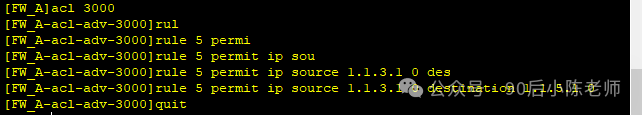
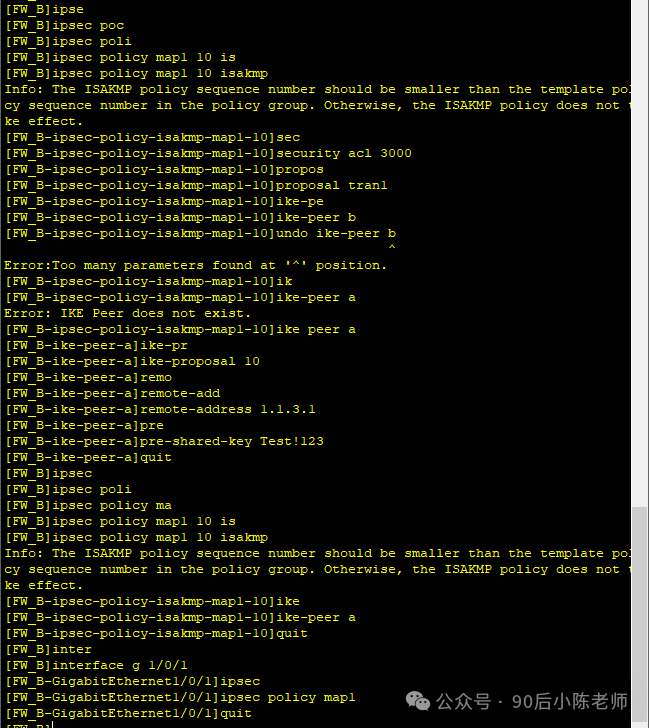
步骤4:防火墙A配置IPSec
(1)创建ACL,匹配GRE隧道流量
(2)IKE安全提议
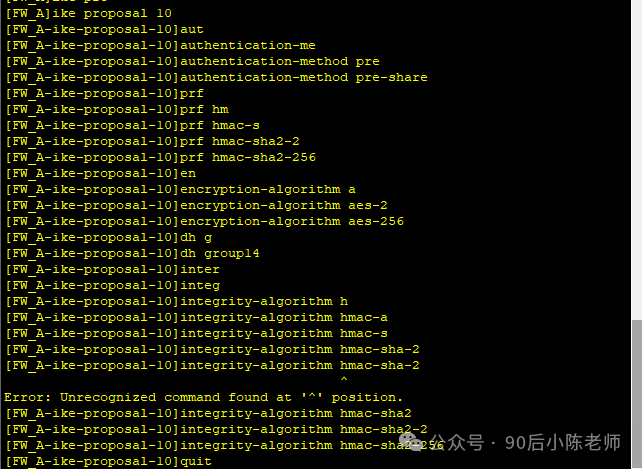
(3)IKE Peer
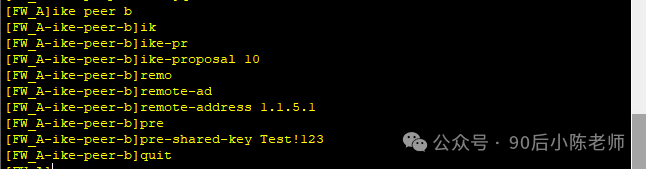
(4)IPSec安全提议
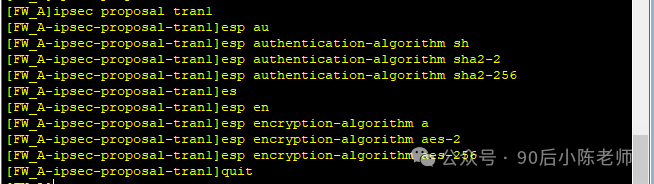
(5)ISAKMP方式的IPSec安全策略

(6)接口应用IPSec策略组

步骤5:配置防火墙B
同防火墙A思路一致,这里省去详细分解步骤
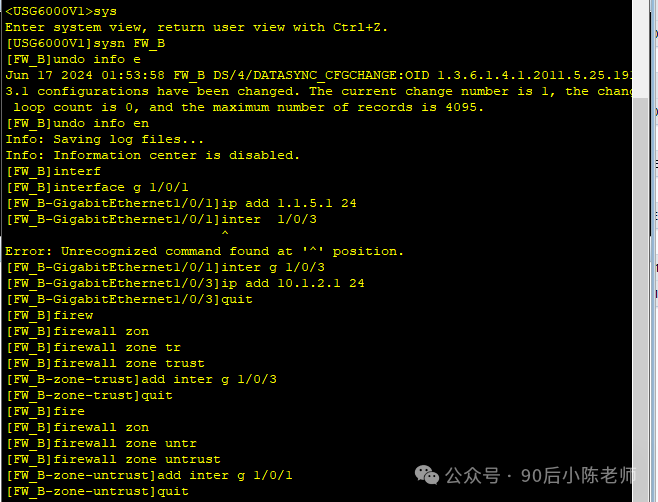


步骤6:配置其他设备
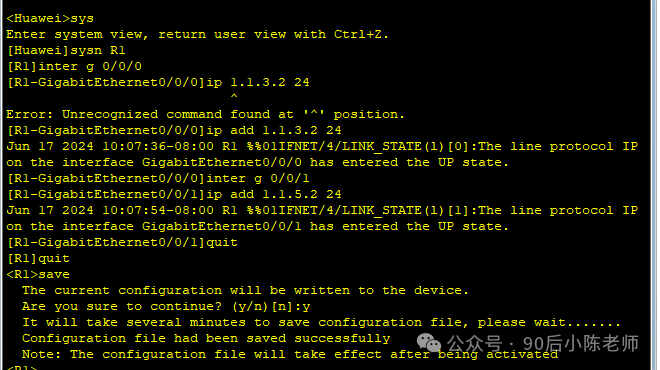
路由器
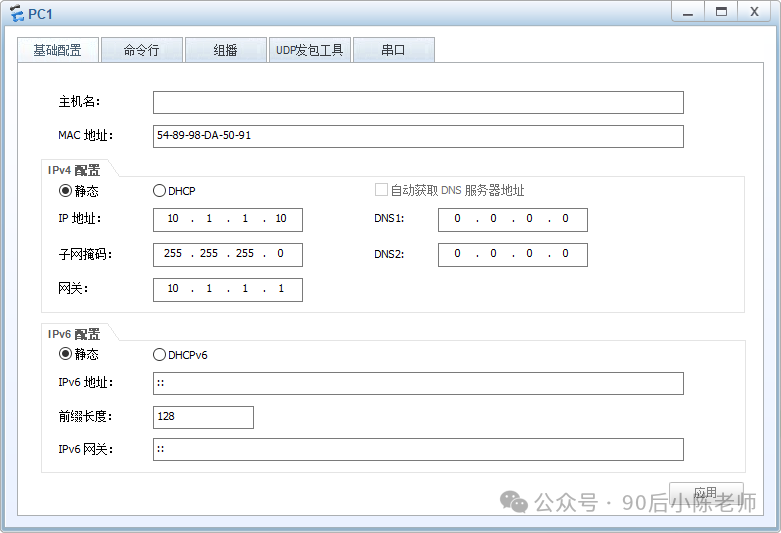
PC
步骤7:验证和调试
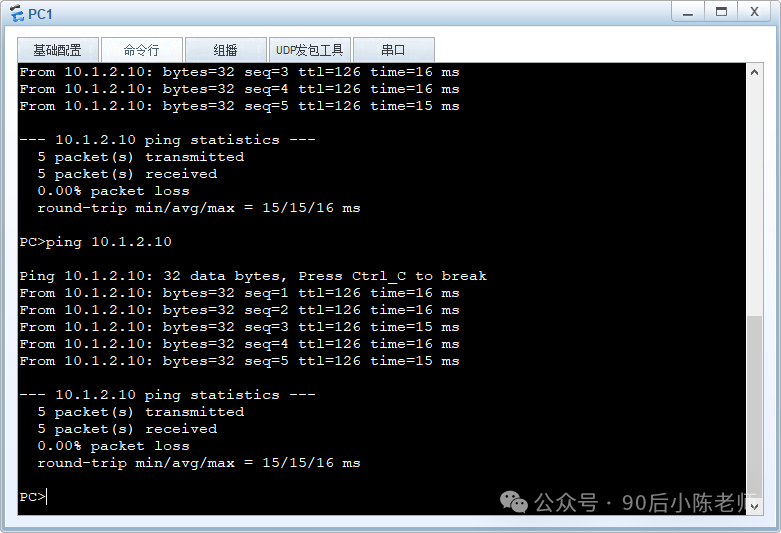
(1)PC1 ping PC2
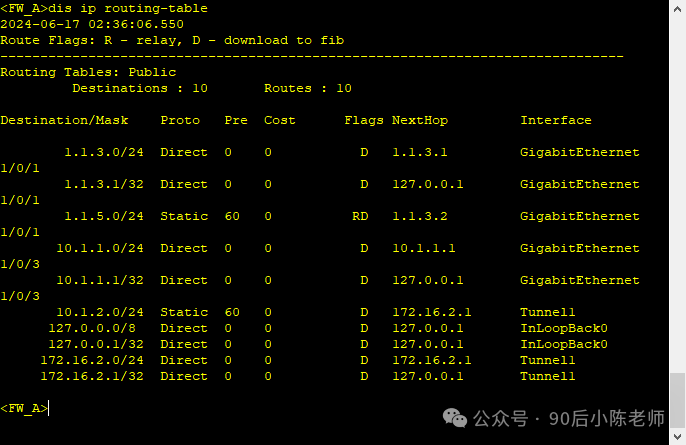
(2)查看路由表
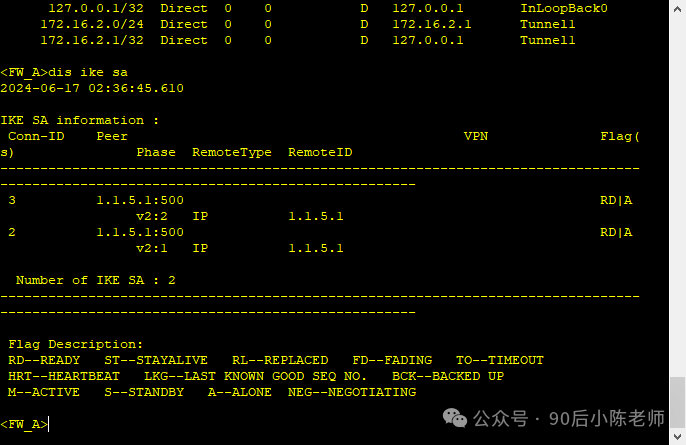
(3)查看IKE SA
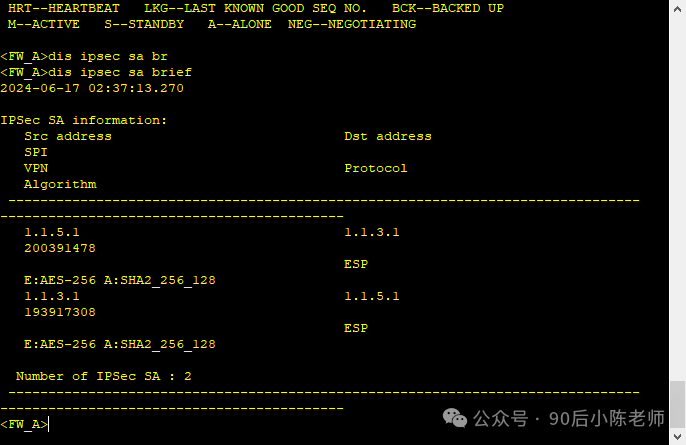
(4)查看IPSec SA
二、设备完整配置
防火墙A
2024-06-17 02:46:41.570 !Software Version V500R005C10SPC300 # sysname FW_A # l2tp domain suffix-separator @ # undo info-center enable # ipsec sha2 compatible enable # undo telnet server enable undo telnet ipv6 server enable # update schedule location-sdb weekly Sun 07:54 # firewall defend action discard # banner enable # user-manage web-authentication security port 8887 undo privacy-statement english undo privacy-statement chinese page-setting user-manage security version tlsv1.1 tlsv1.2 password-policy level high user-manage single-sign-on ad user-manage single-sign-on tsm user-manage single-sign-on radius user-manage auto-sync online-user # web-manager security version tlsv1.1 tlsv1.2 web-manager enable web-manager security enable # firewall dataplane to manageplane application-apperceive default-action drop # undo ips log merge enable # decoding uri-cache disable # update schedule ips-sdb daily 03:35 update schedule av-sdb daily 03:35 update schedule sa-sdb daily 03:35 update schedule cnc daily 03:35 update schedule file-reputation daily 03:35 # ip vpn-instance default ipv4-family # time-range worktime period-range 08:00:00 to 18:00:00 working-day # acl number 3000 rule 5 permit ip source 1.1.3.1 0 destination 1.1.5.1 0 # ipsec proposal tran1 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal default encryption-algorithm aes-256 aes-192 aes-128 dh group14 authentication-algorithm sha2-512 sha2-384 sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 ike proposal 10 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer b pre-shared-key %^%#>%+/NGg=Y0Kmb\CadIHCE>`~Tn<Oh0;Dp~<{7WNB%^%# ike-proposal 10 remote-address 1.1.5.1 # ipsec policy map1 10 isakmp security acl 3000 ike-peer b proposal tran1 # aaa authentication-scheme default authentication-scheme admin_local authentication-scheme admin_radius_local authentication-scheme admin_hwtacacs_local authentication-scheme admin_ad_local authentication-scheme admin_ldap_local authentication-scheme admin_radius authentication-scheme admin_hwtacacs authentication-scheme admin_ad authorization-scheme default accounting-scheme default domain default service-type internetaccess ssl-vpn l2tp ike internet-access mode password reference user current-domain manager-user audit-admin password cipher @%@%z*r:@GKUp.f!{!$'j@:NlU:D%$f#=(HHH%]hpMOuP-zIU:Gl@%@% service-type web terminal level 15manager-user api-admin
password cipher @%@%fB2y%MmXAXt&7y:/(<F@'b{|w#9fraxI=fpr6*!oIBb{-'@%@%
level 15manager-user admin
password cipher @%@%yUbq"G$={FellfRx^4}J7Hb@PO,5+t=mCFBcN}CBi&#ZHbC7@%@%
service-type web terminal
level 15role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-adminl2tp-group default-lns
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METHinterface GigabitEthernet1/0/0
undo shutdowninterface GigabitEthernet1/0/1
undo shutdown
ip address 1.1.3.1 255.255.255.0
ipsec policy map1interface GigabitEthernet1/0/2
undo shutdowninterface GigabitEthernet1/0/3
undo shutdown
ip address 10.1.1.1 255.255.255.0interface GigabitEthernet1/0/4
undo shutdowninterface GigabitEthernet1/0/5
undo shutdowninterface GigabitEthernet1/0/6
undo shutdowninterface Virtual-if0
interface NULL0
interface Tunnel1
ip address 172.16.2.1 255.255.255.0
tunnel-protocol gre
source 1.1.3.1
destination 1.1.5.1firewall zone local
set priority 100firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/3firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Tunnel1firewall zone dmz
set priority 50ip route-static 1.1.5.0 255.255.255.0 1.1.3.2
ip route-static 10.1.2.0 255.255.255.0 Tunnel1undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1firewall detect ftp
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20pki realm default
sa
location
multi-linkif
mode proportion-of-weightright-manager server-group
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-groupuser-manage server-sync tsm
security-policy
rule name policy1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 10.1.2.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.2.0 mask 255.255.255.0
action permit
rule name policy2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 1.1.3.1 mask 255.255.255.255
source-address 1.1.5.1 mask 255.255.255.255
destination-address 1.1.3.1 mask 255.255.255.255
destination-address 1.1.5.1 mask 255.255.255.255
action permitauth-policy
traffic-policy
policy-based-route
nat-policy
quota-policy
pcp-policy
dns-transparent-policy
rightm-policy
return
防火墙B
2024-06-17 02:48:15.350
!Software Version V500R005C10SPC300sysname FW_B
l2tp domain suffix-separator @
undo info-center enable
ipsec sha2 compatible enable
undo telnet server enable
undo telnet ipv6 server enableupdate schedule location-sdb weekly Sun 01:04
firewall defend action discard
banner enable
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-userweb-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enablefirewall dataplane to manageplane application-apperceive default-action drop
undo ips log merge enable
decoding uri-cache disable
update schedule ips-sdb daily 22:10
update schedule av-sdb daily 22:10
update schedule sa-sdb daily 22:10
update schedule cnc daily 22:10
update schedule file-reputation daily 22:10ip vpn-instance default
ipv4-familytime-range worktime
period-range 08:00:00 to 18:00:00 working-dayacl number 3000
rule 5 permit ip source 1.1.5.1 0 destination 1.1.3.1 0ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256ike peer b
pre-shared-key %^%#Pctp(jNAJSW%=.QdUJ%OP/q/>Zr.V'v,+$0:*=0<%^%#
ike-proposal 10
remote-address 1.1.3.1
ike peer a
pre-shared-key %^%#U$8%Trj=@\;]=="5zR"B__7N~i*"3uo}S-SKhn%^%#
ike-proposal 10
remote-address 1.1.3.1ipsec policy map1 10 isakmp
security acl 3000
ike-peer a
proposal tran1aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%5O10&f8mm;)hfV;DCyj5\O^\JJv\U}|X8X%$|OKI/vQNO^_@%@%
service-type web terminal
level 15manager-user api-admin
password cipher @%@%t4v;WkGY4c@}'Ik2z0+2(o^AL!1Cxyh8$r4@ZZK_/6(oa2@%@%
level 15manager-user admin
password cipher @%@%"('Z1A6X86+!u|1('xVPo\wkL`m;B19BbPbH>Z!Ef^R:\wno@%@%
service-type web terminal
level 15role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-adminl2tp-group default-lns
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METHinterface GigabitEthernet1/0/0
undo shutdowninterface GigabitEthernet1/0/1
undo shutdown
ip address 1.1.5.1 255.255.255.0
ipsec policy map1interface GigabitEthernet1/0/2
undo shutdowninterface GigabitEthernet1/0/3
undo shutdown
ip address 10.1.2.1 255.255.255.0interface GigabitEthernet1/0/4
undo shutdowninterface GigabitEthernet1/0/5
undo shutdowninterface GigabitEthernet1/0/6
undo shutdowninterface Virtual-if0
interface NULL0
interface Tunnel1
ip address 172.16.2.2 255.255.255.0
tunnel-protocol gre
source 1.1.5.1
destination 1.1.3.1firewall zone local
set priority 100firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/3firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
add interface Tunnel1firewall zone dmz
set priority 50ip route-static 1.1.3.0 255.255.255.0 1.1.5.2
ip route-static 10.1.1.0 255.255.255.0 Tunnel1undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1firewall detect ftp
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20pki realm default
sa
location
multi-linkif
mode proportion-of-weightright-manager server-group
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-groupuser-manage server-sync tsm
security-policy
rule name policy1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 10.1.2.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.2.0 mask 255.255.255.0
action permit
rule name policy2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 1.1.3.1 mask 255.255.255.255
source-address 1.1.5.1 mask 255.255.255.255
destination-address 1.1.3.1 mask 255.255.255.255
destination-address 1.1.5.1 mask 255.255.255.255
action permitauth-policy
traffic-policy
policy-based-route
nat-policy
quota-policy
pcp-policy
dns-transparent-policy
rightm-policy
return
路由器R1
[V200R003C00]sysname R1
snmp-agent local-engineid 800007DB03000000000000
snmp-agentclock timezone China-Standard-Time minus 08:00:00
portal local-server load portalpage.zip
drop illegal-mac alarm
set cpu-usage threshold 80 restore 75
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %%K8m.Nt84DZ}e#<0`8bmE3Uw}%%
local-user admin service-type httpfirewall zone Local
priority 15interface Ethernet0/0/0
interface Ethernet0/0/1
interface Ethernet0/0/2
interface Ethernet0/0/3
interface Ethernet0/0/4
interface Ethernet0/0/5
interface Ethernet0/0/6
interface Ethernet0/0/7
interface GigabitEthernet0/0/0
ip address 1.1.3.2 255.255.255.0interface GigabitEthernet0/0/1
ip address 1.1.5.2 255.255.255.0interface NULL0
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20wlan ac
return
PC