虽然只做了两道题,但是这两道题里各自有比较新鲜的知识点,值得记录一下
Yusapapa
查看题目所给网站的源码,其中有一段注释
Maybe these texts are really helpful for you
Biometric list is OK!
endow gremlin indulge bison flatfoot fallout goldfish bison hockey fracture fracture bison goggles jawbone bison flatfoot gremlin glucose glucose fracture flatfoot indoors gazelle gremlin goldfish bison guidance indulge keyboard keyboard glucose fracture hockey bison gazelle goldfish bison cement frighten gazelle goldfish indoors buzzard highchair fallout highchair bison fallout goldfish flytrap bison fallout goldfish gremlin indoors frighten fracture highchair bison cement fracture goldfish flatfoot gremlin flytrap fracture buzzard guidance goldfish freedom buzzard allow crowfoot jawbone bison indoors frighten fracture bison involve fallout jawbone Burbank indoors frighten fracture bison guidance gazelle flatfoot indoors indulge highchair fracture bison hockey frighten gremlin indulge flytrap bison flagpole fracture bison indulge hockey fracture flytrap bison allow blockade endow indulge hockey fallout blockade bison gazelle hockey bison inverse fracture highchair jawbone bison gazelle goggles guidance gremlin highchair indoors fallout goldfish indoors bison gazelle goldfish bison indoors frighten gazelle hockey bison flatfoot frighten fallout glucose glucose fracture goldfish freedom fracture blackjack blackjack直接搜下面那一大堆内容,就可以找到是PGP词汇表,对着表替换一下,得到
59 6F 75 20 63 61 6E 20 73 65 65 20 6D 79 20 63 6F 6C 6C 65 63 74 69 6F 6E 20 70 75 7A 7A 6C 65 73 20 69 6E 20 2F 68 69 6E 74 2E 72 61 72 20 61 6E 64 20 61 6E 6F 74 68 65 72 20 2F 65 6E 63 6F 64 65 2E 70 6E 67 2E 0A 42 79 20 74 68 65 20 77 61 79 2C 74 68 65 20 70 69 63 74 75 72 65 20 73 68 6F 75 64 20 62 65 20 75 73 65 64 20 0A 22 59 75 73 61 22 20 69 73 20 76 65 72 79 20 69 6D 70 6F 72 74 61 6E 74 20 69 6E 20 74 68 69 73 20 63 68 61 6C 6C 65 6E 67 65 21 21cyberchef自动解一下,得到
You can see my collection puzzles in /hint.rar and another /encode.png.
By the way,the picture shoud be used
"Yusa" is very important in this challenge!!根据给的目录,下载得到hint.rar和encode.png,在网站首页源码中还可以发现一个encode.webp,也保存下来
解webp文件隐写用到stegpy,无密钥直接解,可以得到压缩包密码
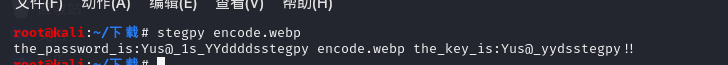
压缩包密码:Yus@_yydsstegpy!!
根据题目所给hint,找到一个加密工具:InvisibleSecret
用Unhide Files选项,选择hint.jpg,选择Blowfish加密,密钥为Yusa,解得一个加密脚本,根据加密脚本写解密脚本,得到flag
from PIL import Image,ImageDraw
hide=Image.open('encode.png').convert('RGB')
R=[]
G=[]
B=[]
a,b = hide.size
for x in range(a):
for y in range(b):
R.append(hide.getpixel((x,y))[0] & 1)
G.append(hide.getpixel((x,y))[1] & 1)
B.append(hide.getpixel((x,y))[2] & 1)
flag = [r^g^b for r,g,b in zip(R,G,B)]
for i in range(len(flag)):
if flag[i] == 1:
flag[i] = 255
en_p = Image.new('L',(a,b),255)
for x in range(a):
for y in range(b):
en_p.putpixel((x,y),(flag[y+x*b]))
en_p.save('flag.png')

Barbar
分离附件二维码后的压缩包,可以得到一个加密的压缩包,提示密钥32位,无法爆破
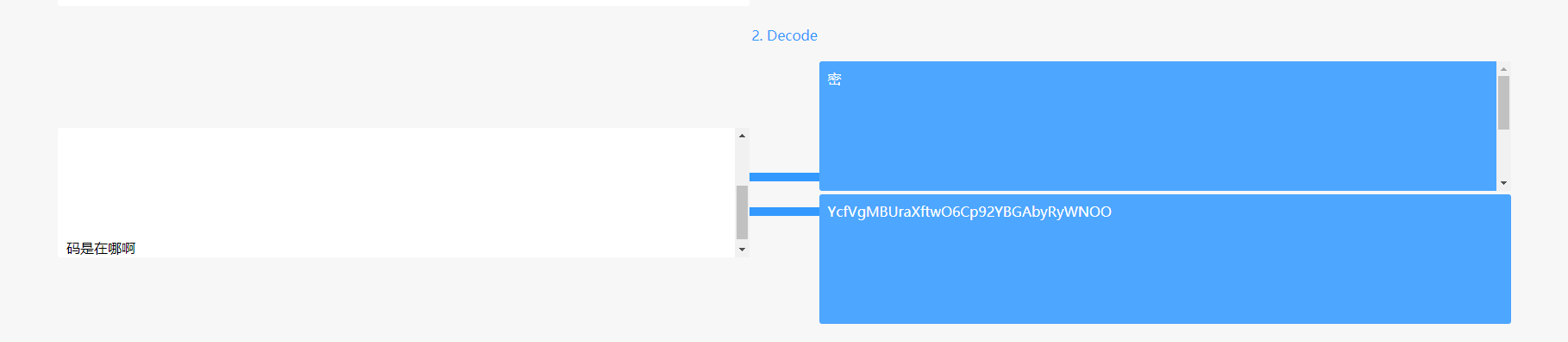
扫码可以发现在密和码之前还藏有其他信息
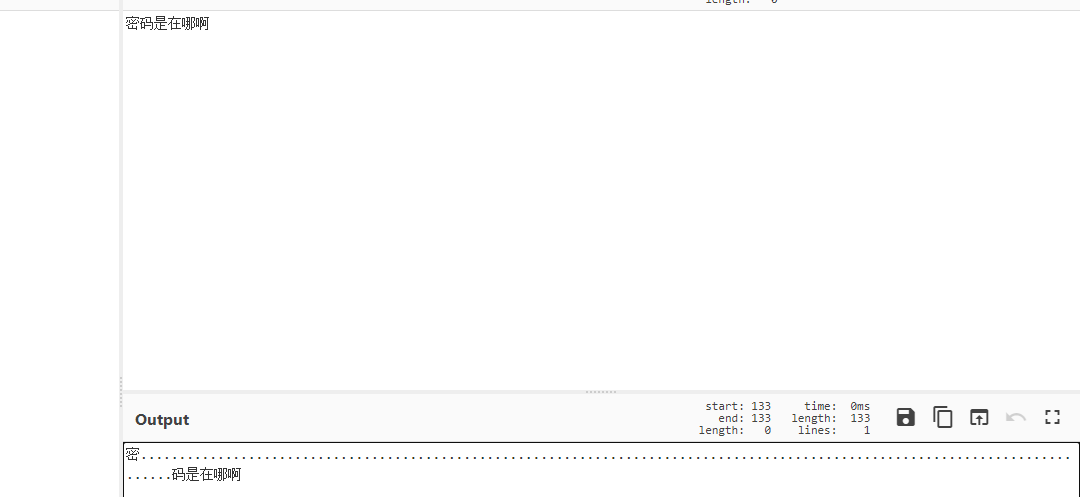
很明显的零宽度字符隐写,可以用vim查看
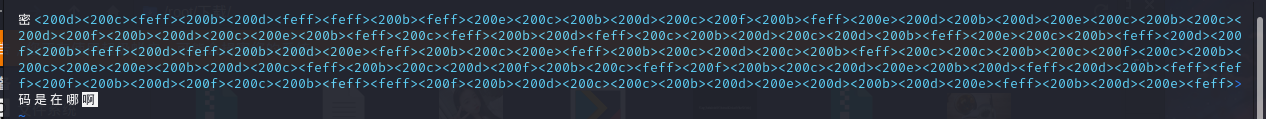
常用的几个零宽度字符隐写的网站都试一下,在此网站可以解得隐藏的信息
解压得到一个坏了的qrcode和一个word文档,先看word文档,里面内容没有什么隐写的地方,所以想到把后缀改成zip,依次查看里面的文件,在document.xml这个文件里可以发现一大串base64
iVBORw0KGgoAAAANSUhEUgAAAGwAAABsCAYAAACPZlfNAAAAAXNSR0IArs4c6QAAAARnQU1BAACx
jwv8YQUAAAAJcEhZcwAAEnQAABJ0Ad5mH3gAAAckSURBVHhe7ZHRauw6EATv///0uX4QRi7NqtIZ
e5OQFBQL6u5xIP8d/NtpVJtZ8ttzw/bH27VAjWozS357btj+eLsWqFFtZslvzw3bH2/XAjWqzSz5
7blh++PtWjCNtG9079meOSWWE+szp+R4q4uvNNK+0b1ne+aUWE6sz5yS460uvtJI+0b3nu2ZU2I5
sT5zSo63uvhKI+0b3Xu2Z06J5cT6zCk53rSwzQ3uKbGcsJ9Kqs6sYX3mJjnetLDNDe4psZywn0qq
zqxhfeYmOd60sM0N7imxnLCfSqrOrGF95iY53rSwzQ3uKbGcsJ9Kqs6sYX3mJvG/ANjBFLuX5iZJ
81RSdWYNb4D0A4bdS3OTpHkqqTqzhjdA+gHD7qW5SdI8lVSdWcMbIP2AYffS3CRpnkqqzqyhDTto
ObE+c0qqzuzdVN+YJVVnllSdi6P3Eg6I5cT6zCmpOrN3U31jllSdWVJ1Lo7eSzgglhPrM6ek6sze
TfWNWVJ1ZknVuTh6L+GAWE6sz5ySqjN7N9U3ZknVmSVV5+LofRgeuBvep6Tq7Ezp7gnvUSP+C9IP
pPA+JVVnZ0p3T3iPGvFfkH4ghfcpqTo7U7p7wnvUiP+C9AMpvE9J1dmZ0t0T3qOGNtKDXex7zFNJ
NyfWZ07J0hnvL+Hgaex7zFNJNyfWZ07J0hnvL+Hgaex7zFNJNyfWZ07J0hnvL+Hgaex7zFNJNyfW
Z07J0hnvJyykcH+3JM2pYX3LSdony6J9EPu7JWlODetbTtI+WRbtg9jfLUlzaljfcpL2ybJoH8T+
bkmaU8P6lpO0T+IFP0hTqhsdieXG3XuTLJ3x/mGWAzClutGRWG7cvTfJ0hnvH2Y5AFOqGx2J5cbd
e5MsnfH+YZYDMKW60ZFYbty9N8nSGe8nLJA0//OqYf2/f9ibNaz/9w97s4b1//5hb9aw/vF2LZik
6symdPdd7PvMTeMT/evAJFVnNqW772LfZ24an+hfByapOrMp3X0X+z5z0/hE/zowSdWZTenuu9j3
mZtG3B+/J/EB9GmK7Zl3JVVn1rB+Ox+/JzYg7NMU2zPvSqrOrGH9dj5+T2xA2KcptmfelVSdWcP6
7Xz8ntiAsE9TbM+8K6k6s4b1b8j3BcK+mWJ7yw3bM6fvpvgbrg8G+2aK7S03bM+cvpvib7g+GOyb
Kba33LA9c/puir/h+mCwb6bY3nLD9szpu1n+hvF+wgKxnNzd/245Nayv+fg90YHk5O7+d8upYX3N
x++JDiQnd/e/W04N62s+fk90IDm5u//dcmpYX/Px+xI7kGL3urlhe+aUVJ2dxHKijfSgYfe6uWF7
5pRUnZ3EcqKN9KBh97q5YXvmlFSdncRyoo30oGH3urlhe+aUVJ2dxHKyNNIDBu+lkqrTkVjexe5r
Pn5PbJDCe6mk6nQklnex+5qP3xMbpPBeKqk6HYnlXey+5uP3xAYpvJdKqk5HYnkXu/+BXAvbnLDf
9d3Y9y03bM+88PpALCfsd3039n3LDdszL7w+EMsJ+13fjX3fcsP2zAuvD8Rywn7Xd2Pft9ywPfPC
64PBPiWWE/Z/mk9zfCP7IPuUWE7Y/2k+zfGN7IPsU2I5Yf+n+TTHN7IPsk+J5YT9n+bTLF+o/ohZ
Yjnp9rsSy1PsHnOTLC/VaJZYTrr9rsTyFLvH3CTLSzWaJZaTbr8rsTzF7jE3yfJSjWaJ5aTb70os
T7F7zE2yvNggJb3HPjWsz5waT/eN5cLtHwjvsU8N6zOnxtN9Y7lw+wfCe+xTw/rMqfF031gu3P6B
8B771LA+c2o83TeOG9lB9mlKdWOnYf00f1pSdeD1wWCfplQ3dhrWT/OnJVUHXh8M9mlKdWOnYf00
f1pSdeD1wWCfplQ3dhrWT/OnJVXn4uh9GB4g3ZywbxLLifWZd02JF/bBbk7YN4nlxPrMu6bEC/tg
Nyfsm8RyYn3mXVPihX2wmxP2TWI5sT7zrim6sA+kOTWqzaxRbWZTunvCe5ToF/VAmFOj2swa1WY2
pbsnvEeJflEPhDk1qs2sUW1mU7p7wnuU6Bf1QJhTo9rMGtVmNqW7J7xHyfJiA4P71BTbW07YTzWs
r/n4PbGBwX1qiu0tJ+ynGtbXfPye2MDgPjXF9pYT9lMN62s+fk9sYHCfmmJ7ywn7qYb1P5DvC8T6
lhu27+aG7bs5sT7zw+uDYX3LDdt3c8P23ZxYn/nh9cGwvuWG7bu5YftuTqzP/PD6YFjfcsP23dyw
fTcn1md+eH0gzCmpOrOk6sySNKeG9ZlTo9rsJMebFraSqjNLqs4sSXNqWJ85NarNTnK8aWErqTqz
pOrMkjSnhvWZU6Pa7CTHmxa2kqozS6rOLElzalifOTWqzU6yvOgAuUksN57ef3VuLAs7yNwklhtP
7786N5aFHWRuEsuNp/dfnRvLwg4yN4nlxtP7r873/Pv3P5ySkc0n6rmgAAAAAElFTkSuQmCC解码后发现是个png,转成png是一个aztec码,扫码可得
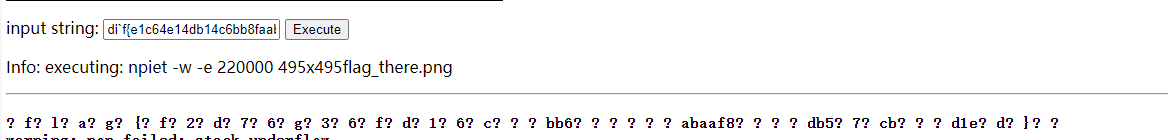
di`f{e1c64e14db14c6bb8faabab5bd7be1dc}再看那个损坏的qrcode,只缺少了三个定位码,补全即可扫出来,但是扫码并不能得到任何有用信息,也没有零宽隐写,所以需要转换思路,观察这个损坏的二维码的图案,实际上是一种基于颜色和像素的编程语言:piet
这种编程语言有在线的解释器,搜索npiet即可找到:https://www.bertnase.de/npiet/npiet-execute.php
上传图片,选择最下面的那个选项

在input string处输入通过aztec码得到的那串和flag极为相似的字符串,点击运行,即可得到flag